Click here to get this post in PDF
As ransomware becomes an increasingly lucrative business, organized crime groups are expanding their operations to reach more victims and extract more ransoms. According to the FBI, ransomware costs are now $ 1 billion/year just for payments, not including remediation costs.
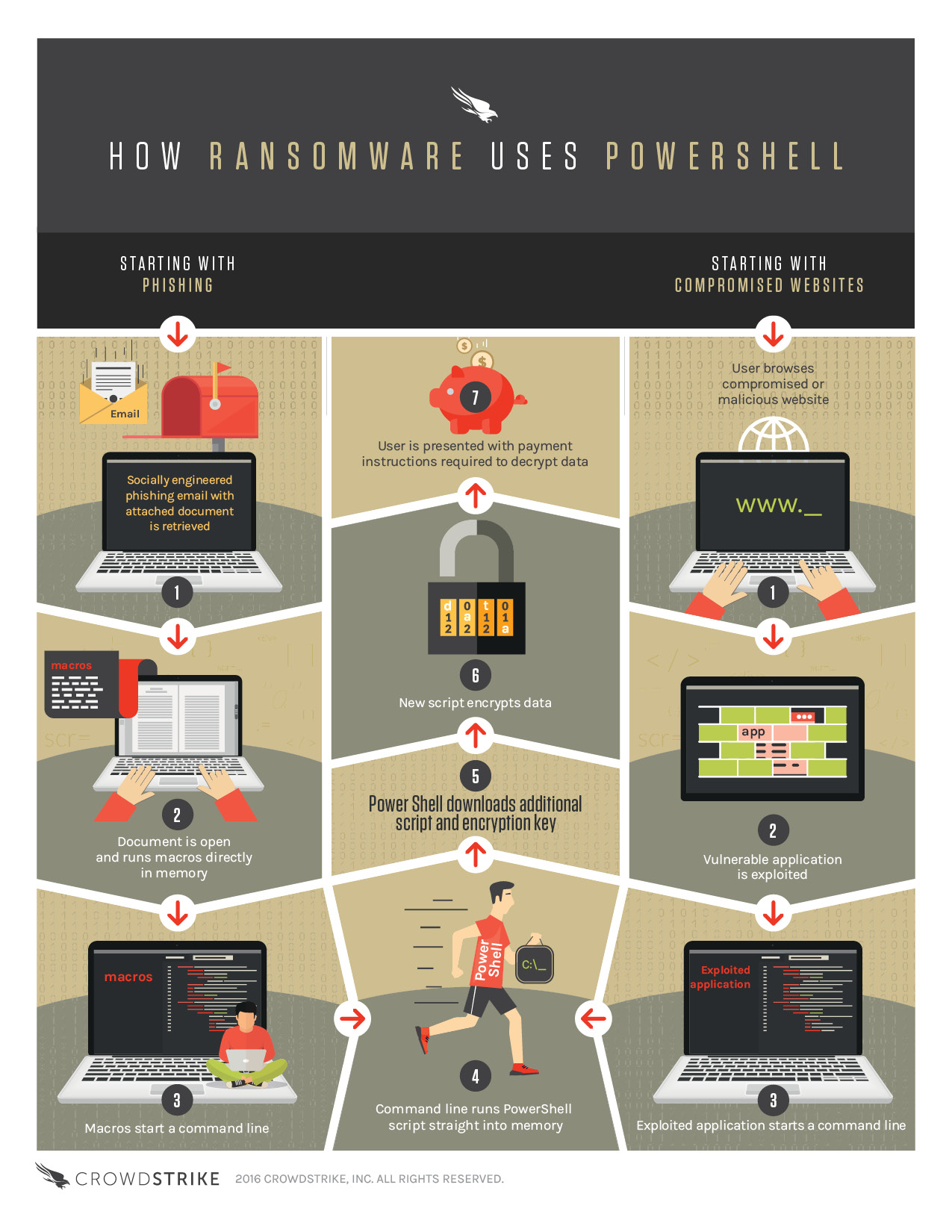
Fileless ransomware refers to a type of malicious software that operates without leaving traditional traces on the victim’s computer system, such as files or executables. Instead, it leverages legitimate tools already present on the system, like PowerShell, to carry out its malicious activities. PowerShell is a scripting language and automation framework available on Windows systems, making it an attractive choice for attackers.
Here’s a general overview of how fileless PowerShell-based ransomware works:
Initial compromise: The attacker gains access to the victim’s system through various means, such as phishing emails, compromised websites, or exploit kits. Once inside, the attacker typically performs reconnaissance to identify potential targets and vulnerabilities.
Execution through PowerShell: Instead of dropping malicious files onto the victim’s system, the attacker utilizes PowerShell, a legitimate and powerful scripting language present on most Windows machines. PowerShell allows for the automation of system administration tasks but can also be misused for malicious purposes.
Script execution: The attacker crafts a PowerShell script containing the ransomware’s malicious code. This script may be obfuscated to evade detection by antivirus software. The script is then executed using legitimate PowerShell commands or techniques like “Invoke-Expression” or “Invoke-Command.”
Memory-based payload: The ransomware resides solely in the system’s memory without writing files to the disk. This makes it harder for traditional antivirus solutions to detect malicious activity, as there are no suspicious files to scan.
Elevation of privileges: To gain sufficient privileges for system-wide access and to bypass security measures, the ransomware script may attempt to escalate its privileges using techniques like abusing Windows Management Instrumentation (WMI) or exploiting vulnerabilities in the operating system.
Encryption and ransom note: Once the ransomware gains control, it encrypts the victim’s files using encryption algorithms. The encryption keys may be generated on the attacker’s command-and-control (C&C) server or using asymmetric encryption to ensure they are difficult to decrypt without the proper key. After encryption, the ransomware presents a ransom note, typically demanding payment in cryptocurrency in exchange for the decryption key.
Persistence and propagation: Fileless ransomware may establish persistence on the compromised system, ensuring it survives reboots or attempts to remove it. It may also attempt to propagate to other machines on the network, using techniques like lateral movement or exploiting vulnerabilities in shared resources.
Preventing and mitigating fileless PowerShell-based ransomware requires a multi-layered approach, including robust security practices such as user education, strong email filtering, regular software patching, network segmentation, and monitoring for suspicious PowerShell activities. Additionally, deploying advanced endpoint protection solutions capable of detecting and blocking fileless attacks is crucial.
Also read: Cybersecurity – The Most Common Threats to Your Business
This infographic describes how fileless PowerShell-based ransomware works.
How Ransomware Uses Powershell provided by CrowdStrike