Click here to get this post in PDF
Looking beyond darknet, ready to shift left!
Exploring the dark side of the web is a tough job. Also, taking initiatives to preempt malicious cyber-attacks requires proactive measures rather than merely reactive procedures.
Many internet frauds such as phishing, data leaks, blackmail, and other cybercrimes are inevitable for every business. So, is there any solution to provide a real-time strategy to preempt further cyber threats? Should we get ambushed by anonymous intruders or take necessary actions before they catch our sensitive data in the blink of an eye?
Threat intelligence is an excellent solution for cyber-attacks. It is a strategy to guard your data against unknown security breachers. It gathers vital information to prepare for potential cyber-attacks. Happily, several technologies have been introduced in recent years to improve vulnerability and protect from cybercriminals. Here are the latest innovations in cyber threat Intelligence. Let’s dive into what exactly they are.
DVE score, a brand-new vulnerability exploration tracker
To forestall possible cyber-attacks, a systematic procedure is needed. DVE score (Dynamic Vulnerability Exploit) is one of the newest procedures to provide vulnerability management solutions. It is developed by Cybersixgill, a pioneering company in cybercriminal detection automation.
DVE score is a tool to help the security team identify and evaluate vulnerable security holes in a network or system. It uses AI analysis to track Common Vulnerabilities and Exposures (CVEs) and read threat actors’ intentions in the dark web. The primary benefit of this innovation is that you can integrate it with other security platforms such as TIP, SIEM, and SOAR.
Continuous Investigation/Continuous Protection (CI/CP)
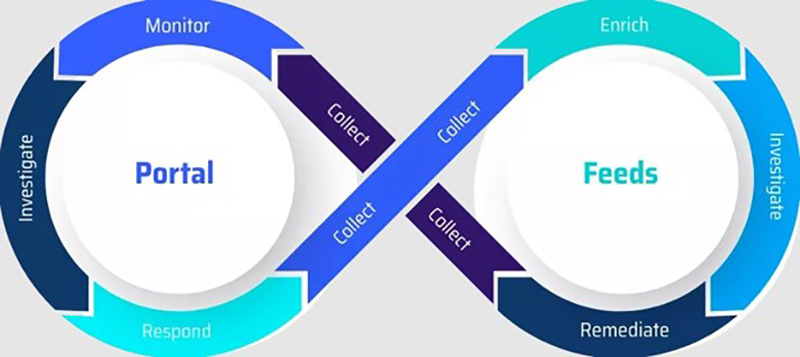
CI/CP acts as two wings of agile threat intelligence methodology for quicker preemptive responses. They utilize automation tools to collect information to anticipate threat actors’ behavior. CI employs an investigative portal to discover valuable TTP, related IP and domains, hacker tools, and contact information. CP is an exclusive utility of the Cybersixgill program that provides seamless protection to categorize them for further threat analysis.
Behavioral Analytics and IOCs for detecting financial fraud
Behavioral Analytics is a novel method that combines Al and big data to analyze user trends. It is widely used in E-commerce to predict consumers behaviors. However, you can use it as a cybersecurity tool to keep a beady eye on cyber phishers.
Moreover, you can detect any anomalies in the financial system with Indicators of Compromise (IOCs). It is slightly similar to the behavioral Analytics mechanism. IOC uses a tracking system stored in log files. So, you use clues in the log files to find traces of attackers. Several companies, including Cybersixgill groups, recently offered financial fraud detection systems. With this innovative method, you can investigate IOCs and prepare in-depth well-organized phishing and fraud reports for further analysis.
SIM swap protection from scammers
Two-step verification plays a vital role in securing your account privacy by sending SMS to SIM. SIM swaps occur when hackers trick your phone carrier and steal your phone number. Then, the hacker will control any account logged in by SIM, including your email or bank account.
To resolve this issue, many companies provide customers with exclusive anti-swapping services to call their SIM cards or protect them against telecommunication hackers. Cybersixgill is one of the leading companies that offer SIM security solutions to telecom carriers. This service is indispensable for every mobile service provider since it warns them against SIM swappers.
Final words
Cyber Threat Intelligence is a tactical procedure to safeguard the business from cyber-attacks. It enjoys new technologies to warn companies of likely cyber crimes such as phishing, sensitive data leakage, vulnerability exploitation, and SIM swapping. Happily, several innovations, including Cybersixgill DVE score and CI/CP, have been introduced to protect businesses from hackers.
You may also like: Data Privacy Experts and Cybersecurity Professionals Predict Privacy Trends for 2022